Then you have to configure one default route on the switch: ip route 0.0.0.0 0.0.0.0 10.0.0.1 (assume ASA internal IP is 10.0.0.1). For this option, you will NOT have any problems on the ASA by configuring object groups for networks that are not directly connected on the ASA. E.g if one internal vlan has subnet 10.1.1.x, then you can configure. Route map entries are read in order. You can identify the order using the sequencenumber argument, or the ASA uses the order in which you add route map entries. Customize a Route Map This section describes how to customize the route map.
The Cisco ASA has some interesting characteristics when dealing with traceroute. With most traffic, including ICMP echo, outbound traffic can be inspected to allow the incoming traffic associated with the same flow. Inspecting 'ICMP' or even 'ICMP Error' does not result in traceroute functioning through the ASA.
The first thing that we need to look at is how traceroute works. Traceroute uses two different types of ICMP packets. Windows systems use an ICMP with incrementing TTL's to illicit an ICMP TTL exceeded message from each hop along the way. Linux and Cisco use a UDP port with pseudorandom destination port. With the UDP method, an incrementing TTL is still used to illicit a message from each hop along the way. However, the message that is produced at the final destination is often an 'ICMP unreachable port-unreachable' message.
Note to reader: All ASA content can be accessed by clicking here (or choosing ASA from the menu at the top of the page).
To understand how traceroute works, it is important to understand the function of the TTL field in the IP packet header. This field is an 8-bit value that works with routers to keep packets from looping forever as a result of network configuration issues. The way this is accomplished is that each router along the way decreases the value by 1. Normal traffic may start out with a TTL of 64, 128, 255 or any other non-zero value. Warcraft version switcher 1.27. As the traffic traverses a router, this TTL in the IP header is reduced by one.
When a router decreases the value to zero, it drops the packet. When this happens the device will respond with an 'ICMP TTL exceeded' if it is in response to an ICMP packet. If a TCP or UDP packet makes it to the final destination without that port listening, the host will respond with an 'ICMP Unreachable/Port-Unreachable'. It is worth noting that any device can usually be configured to not respond at all.
Traceroute takes advantage of this behavior and generates a series of packets. The first packet(s) will have a TTL of one and be dropped by the first router. The next packet(s) will have a TTL of two and be dropped by the second router. This is used to build a map of the network. If there is a device configured not to respond traceroute will indicate the presence of a device, but its IP address will not be identified.
With our default ASA configuration, let's see if traceroute will work.
Asa Route Map Colorado
Windows PC

Asa Route Map San Francisco
As we can see, there is no intermediary information. We know that we are not receiving the TTL-exceeded messages from the routers in the network. Filmora 9 serial crack. The ASA requires special configuration to permit the traffic. The first challenge is to permit these TTL-exceeded and port unreachable messages back into the network. This can be done by using an ACL bound to the outside interface.
ASA Config
Now let's test traceroute again.
Windows PC
Now that looks much better. However, I can see that my ASA is not listed in the path. That is very strange. Upon investigation, I determine that the ASA itself does not decrease the TTL as it passes traffic. Firewalls often play by slightly different rules than a router and this is one of those exceptions. However, we can change this behavior using the set connection option in the modular policy framework (MPF).
ASA Config
Now, let's test traceroute again.
Windows PC
We can now see an extra hop (75.117.163.238 is an address on my ASA), but there are missing statistics (see the *). This is a result of the fact that the ASA is not responding to all of the traceroute packets. This is due to the rate-limiting of ICMP on the ASA. We can adjust this as well.
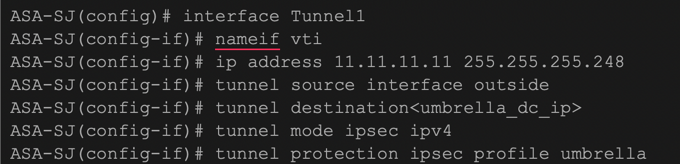
ASA Config
ASA Config
Now we can run our test again.
Windows PC

We can see the issue has resurfaced. If we have logging enabled, we can see the IDS engine is detecting this as a 'land' attack.
Let's disable just this one signature.
ASA Config
Now we can retest this once again.
Windows PC
Now you can see that we have a successful traceroute configuration on our ASA. So if I were to receive a lab question that says to make sure traceroute will work through my ASA, that question can mean several things. If I get such a question on the lab and it is vague, I will verify with the proctor exactly what a successful traceroute means. I will also keep in mind that if I enable ids on the ASA that I should probably re-check the traceroute to verify it still works.
Asa Route Map Directions
Asa Route Map San Francisco
As we can see, there is no intermediary information. We know that we are not receiving the TTL-exceeded messages from the routers in the network. Filmora 9 serial crack. The ASA requires special configuration to permit the traffic. The first challenge is to permit these TTL-exceeded and port unreachable messages back into the network. This can be done by using an ACL bound to the outside interface.
ASA Config
Now let's test traceroute again.
Windows PC
Now that looks much better. However, I can see that my ASA is not listed in the path. That is very strange. Upon investigation, I determine that the ASA itself does not decrease the TTL as it passes traffic. Firewalls often play by slightly different rules than a router and this is one of those exceptions. However, we can change this behavior using the set connection option in the modular policy framework (MPF).
ASA Config
Now, let's test traceroute again.
Windows PC
We can now see an extra hop (75.117.163.238 is an address on my ASA), but there are missing statistics (see the *). This is a result of the fact that the ASA is not responding to all of the traceroute packets. This is due to the rate-limiting of ICMP on the ASA. We can adjust this as well.
ASA Config
Now let's test this one more time.
Windows PC
Now we can see solid statistics on the first hop. Now our ASA is working correctly with traceroute traffic. I want to show one more example of a way to break traceroute.
Let's set the IP Audit Attack policy on the outside interface.
ASA Config
Now we can run our test again.
Windows PC
We can see the issue has resurfaced. If we have logging enabled, we can see the IDS engine is detecting this as a 'land' attack.
Let's disable just this one signature.
ASA Config
Now we can retest this once again.
Windows PC
Now you can see that we have a successful traceroute configuration on our ASA. So if I were to receive a lab question that says to make sure traceroute will work through my ASA, that question can mean several things. If I get such a question on the lab and it is vague, I will verify with the proctor exactly what a successful traceroute means. I will also keep in mind that if I enable ids on the ASA that I should probably re-check the traceroute to verify it still works.
Asa Route Map Directions
Asa Route-map Configuration
Firepower Administrators should also check out – Traceroute through Firepower Threat Defense.
